
Let me put on my Bond Villain hat for a moment and think about the best way to bring modern society to its knees. And let’s assume I want to pull this off without wiping out humanity in the process; if I wanted to do that there are always nuclear weapons and, at the rate we’re going, just waiting patiently for fifty years. No, this mustache-twirling thought experiment calls for something a little less drastic than turning the planet into a radioactive wasteland, but only just. For the sake of argument, then, how would I go about taking down the Internet for long enough to topple human civilisation?
An Alarming Precedent
Recent high-profile outages highlight the potential impact of throwing any kind of wrench - accidentally or otherwise - into the delicate Swiss watch of the modern internet.
An outage caused by a glitch at service provider Fastly - which runs an edge cloud between companies' data centres and the end users of sites like Amazon, Twitch, and Reddit - “knocked out half the internet” for about an hour in June. The fire at one of OVHcloud’s data centres in Strasbourg left millions of websites offline in March. These outages - albeit briefly - left the internet reeling. And they were both accidents. Imagine what could happen if there was a concerted effort to bring down the internet.
How do I kill the internet?
Based on the kind of research that’s definitely put me on several terrorist watch lists, it seems like there are two main ways to harm the internet in a meaningful sense: cut the cables, and find a way to shut down a surprisingly small number of hyperscale data centres.
Whether either, or both of these methods together, would actually turn it off for good is debatable, but given the level of disruption caused by a faulty server knocking out Reddit for an hour, I think it’s safe to assume that taking down the Internet for a whole month could pretty handily trigger the downfall of human civilisation.
Cut the Wires
This may sound simplistic, but subsea cables are the veins and arteries carrying the lifeblood of the Internet beneath the sea. They represent very physical, tangible targets that are too large to properly defend. There’s even a handy map with a useful list of potential targets available for free on the Internet (et tu, Brutus?).
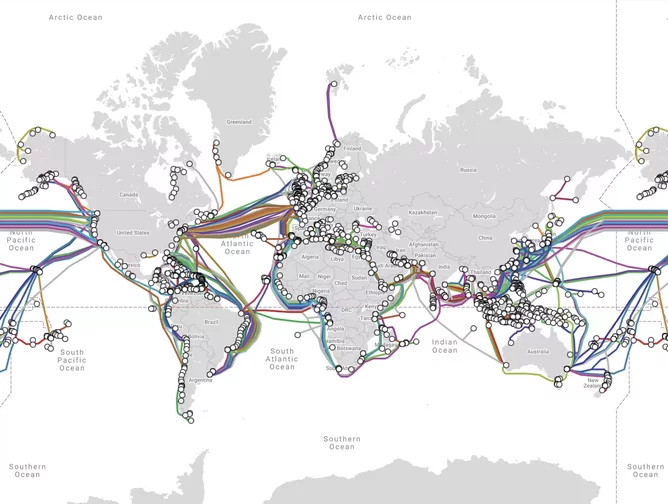
Subsea cables are both a physical and cyber vulnerability of the modern Internet, and roughly 99% of global web traffic depends on them. Of course, as Bill Kleyman (whose name sounds delightfully similar to Hans Gruber’s alias in Die Hard) wrote in a 2014 article, “you can’t just cut the wires. Why? Because they’re designed to be fixed.” However, he adds that...
“A strategic strike that will take out the fibre optic cables or damage the entire wire will do the trick. If this is done at choke points you can disable or almost completely halt global Internet traffic.” - Bill Kleyman

How to take out a hyperscale data centre
Fibre optic cables are also, according to a top exec at a leading data centre brand whose communications team requested he remain anonymous, one of the simplest ways to tackle the second phase of my plan: knocking out some of the world’s biggest data centres.
“One of the easiest ways to knock out a hyperscale data centre would be to target the incoming fibre positions, which are owned and operated by the fibre carrier,” he explains. Then, because this is something he clearly thinks about a lot, he adds: “Another more complicated way would be to run a port scan through the data centre's corporate network to see if there was any bridge between that and the industrial controls networks. If you can locate operational technology devices that control the cooling and power systems, you can shut them down remotely and cripple the data centre as the industrial networking protocols and devices contain no embedded security encryption or measures to protect them.”
Attacks targeting a data centre’s power and cooling systems have been on security professionals’ horizons for over a decade already. In 2014, academics at Ohio State University ran a number of hardware tests and simulations, coming to the conclusion that, with the right malware, you can easily “generate power spikes on multiple servers at the same time, which may cause branch circuit breakers to trip and lead to undesired power outages.”
And getting that malware inside a data centre, the data centre security exec explains, is actually a lot easier than it sounds. “Many systems within data centres, which support the cooling/power and critical infrastructure, require software patches, updates and maintenance, and are based on extremely vulnerable legacy protocols,” he says. “If these are not sufficiently air gapped or secured behind firewalls and DMZ's, they can be easy prey to hackers and malware attackers, essentially attacking the data centre through its own critical infrastructure.”
Darren Watkins, a Managing Director at Virtus Data Centres, was also willing to talk to me about the weaknesses of a modern data centre, although, understandably, he politely refused to give me a step-by-step plan for knocking out one of his facilities. “From a holistic security point of view, the biggest security weakness has to be the security associated with access to the data that is held or being generated within the data centre,” he muses, noting that “This comprises firewalls, software and network security aspects that are the responsibility of the end customer.” Given that some major carrier hotels can host hundreds of different customers of different sizes, the odds that one of them isn’t doing their due diligence with regard to security are troublingly high. Just look at the SolarWinds attack last year, when Russian hackers used access to the company’s Orion software to distribute trojanized updates to the company’s customers, and ended up gaining access to data centres belonging to at least nine US federal agencies, including NASA, the State Department, the Department of Defense, and the Department of Justice.
The Inside Job
Aside from getting malware inside a data centre, one of the most effective ways to cause significant disruption is to type up a resume and get a job.
A CEO from the industry, who elected to remain anonymous, explains to me “The reality is that, other than squirrels taking down data centres (yes it's true, check it out) human error is the biggest reason why it happens. Although Tier III data centers are fed with redundant power feeds, making them ordinarily foolproof, nothing will help if an individual hits the EPO in the switchgear room - a so-called inside job.” They do note, however, that “Most of these facilities have fairly foolproof security systems, and video surveillance would make it challenging to get away with such a dastardly deed.”

In Conclusion…
We can all agree that knocking out the Internet through a coordinated campaign of cyber attacks and strategic raids on subsea cable junctions isn’t a good idea - no matter how much joy the thought of a submarine with a giant pair of wire cutters on the front of it brings both my and my fluffy white cat. I’m a reasonable human being.
But the world isn’t exclusively made up of reasonable human beings. Not by a long shot. In April, the FBI foiled a plot by radical right wing conspiracy theorist Seth Aaron Pendley to use a pipe bomb to blow up a hyperscale AWS data centre in Ashburn, Virginia. Pendley, an avowed QAnon truther, fervent Trump supporter, and participant in the January 6 attack on the US capitol, allegedly planned to “kill off about 70 percent of the Internet” if successful.
While it’s doubtful that, even if he succeeded, the terrorist plot would have been anywhere near that successful, it’s still a sobering thought. What if someone else tries it? Someone a good deal smarter, or richer than Pendley. What if they succeed? The critical infrastructure that underpins our modern world is a lot more fragile than we’d care to admit.






